Difference between revisions of "File:Fig5 Jebali JofInfoTelec2020 5-1.jpg"
From LIMSWiki
Jump to navigationJump to searchShawndouglas (talk | contribs) |
Shawndouglas (talk | contribs) (Added summary.) |
||
| Line 1: | Line 1: | ||
==Summary== | |||
{{Information | |||
|Description='''Figure 5.''' An example of bypassing access control using an inference channel. | |||
|Source={{cite journal |title=Secure data outsourcing in presence of the inference problem: Issues and directions |journal=Journal of Information and Telecommunication |author=Jebali, A.; Sassi, S.; Jemai, A. |volume=5 |issue=1 |pages=16–34 |year=2020 |doi=10.1080/24751839.2020.1819633}} | |||
|Author=Jebali, A.; Sassi, S.; Jemai, A. | |||
|Date=2020 | |||
|Permission=[http://creativecommons.org/licenses/by/4.0/ Creative Commons Attribution 4.0 International] | |||
}} | |||
== Licensing == | == Licensing == | ||
{{cc-by-4.0}} | {{cc-by-4.0}} | ||
Latest revision as of 19:08, 6 April 2021
Summary
| Description |
Figure 5. An example of bypassing access control using an inference channel. |
|---|---|
| Source |
Jebali, A.; Sassi, S.; Jemai, A. (2020). "Secure data outsourcing in presence of the inference problem: Issues and directions". Journal of Information and Telecommunication 5 (1): 16–34. doi:10.1080/24751839.2020.1819633. |
| Date |
2020 |
| Author |
Jebali, A.; Sassi, S.; Jemai, A. |
| Permission (Reusing this file) |
|
| Other versions |
Licensing
|
|
This work is licensed under the Creative Commons Attribution 4.0 License. |
File history
Click on a date/time to view the file as it appeared at that time.
| Date/Time | Thumbnail | Dimensions | User | Comment | |
|---|---|---|---|---|---|
| current | 19:07, 6 April 2021 | 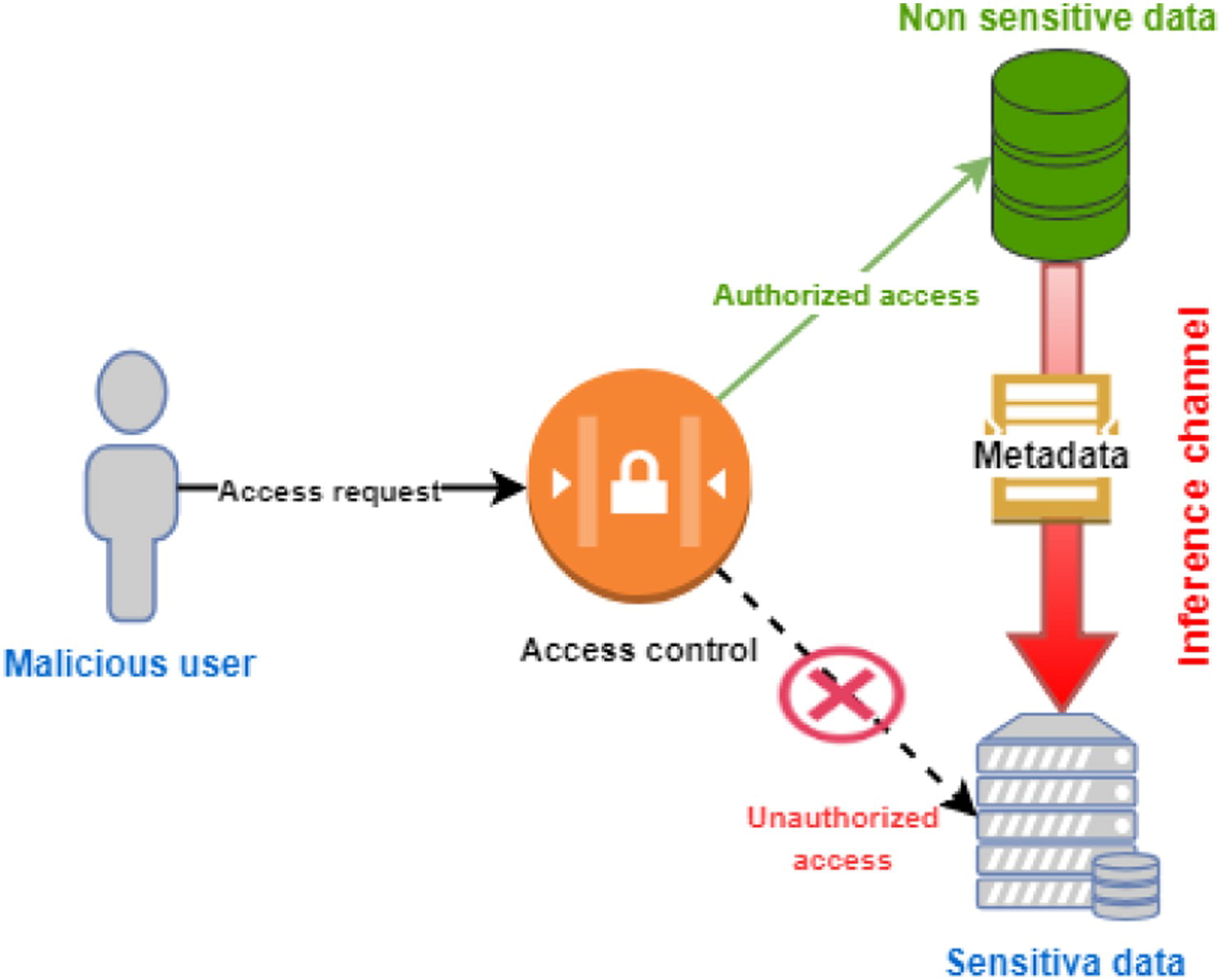 | 1,500 × 1,203 (145 KB) | Shawndouglas (talk | contribs) |
You cannot overwrite this file.
File usage
The following 3 pages use this file:







