Difference between revisions of "File:Cyber table with source.png"
From LIMSWiki
Jump to navigationJump to searchShawndouglas (talk | contribs) (Most Common Types of Cybersecurity Incidents in the U.S.; Dollars in millions. Source: https://www.gao.gov/cybersecurity) |
(No difference)
|
Latest revision as of 23:37, 1 March 2023
Summary
Most Common Types of Cybersecurity Incidents in the U.S.; Dollars in millions. Source: https://www.gao.gov/cybersecurity
Licensing
|
|
This work is in the public domain in the United States because it is a work of the United States Federal Government under the terms of Title 17, Chapter 1, Section 105 of the US Code. Note: This only applies to works of the Federal Government and not to the work of any individual U.S. state, territory, commonwealth, county, municipality, or any other subdivision. This template also does not apply to postage stamp designs published by the United States Postal Service since 1978. (See 206.02(b) of Compendium II: Copyright Office Practices). |
 |
File history
Click on a date/time to view the file as it appeared at that time.
| Date/Time | Thumbnail | Dimensions | User | Comment | |
|---|---|---|---|---|---|
| current | 23:37, 1 March 2023 | 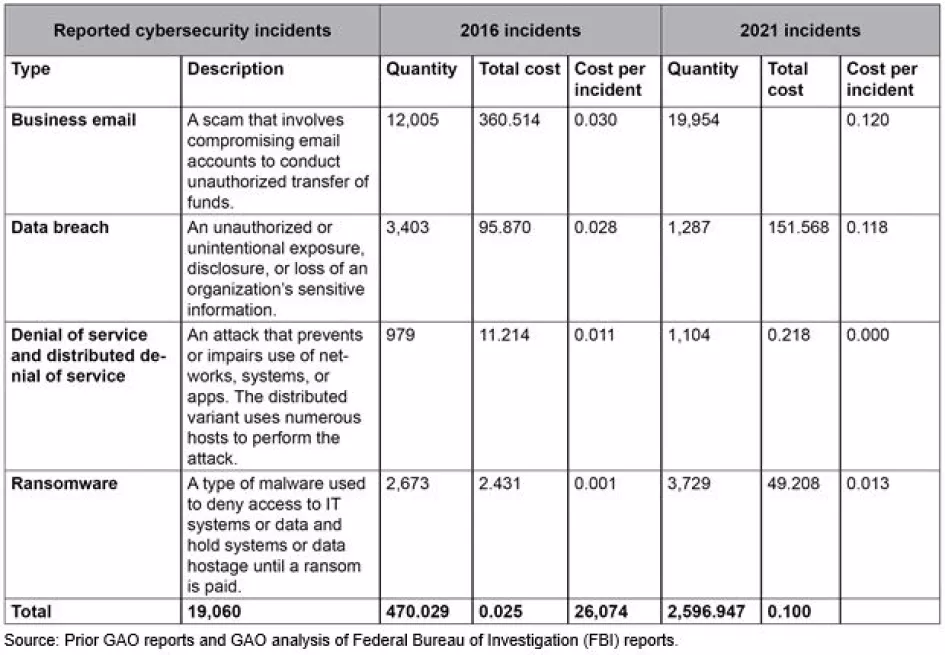 | 945 × 655 (366 KB) | Shawndouglas (talk | contribs) | Most Common Types of Cybersecurity Incidents in the U.S.; Dollars in millions. Source: https://www.gao.gov/cybersecurity |
You cannot overwrite this file.
File usage
The following 3 pages use this file:
- Template:Comprehensive Guide to Developing and Implementing a Cybersecurity Plan/What is a cybersecurity plan and why do you need it?
- LII:Comprehensive Guide to Developing and Implementing a Cybersecurity Plan/What is a cybersecurity plan and why do you need it?
- Book:Comprehensive Guide to Developing and Implementing a Cybersecurity Plan/What is a cybersecurity plan and why do you need it?/Cybersecurity planning and its value







