LabLynx KB:SysAdmin - 4.2 security system setup
|
|
This is an article specific to the Category:LabLynx knowledge base. Its context outside of LabLynx, Inc may not be apparent, thus why it appears inside the LabLynx KB namespace. |
Security system setup
Managing security in installed LIMS software is a vital step, ensuring the integrity of the data collected, analyzed, and stored in your laboratory is maintained. This document continues to discuss security, addressing the concepts of profiles, user lists, passwords, and system picklists.
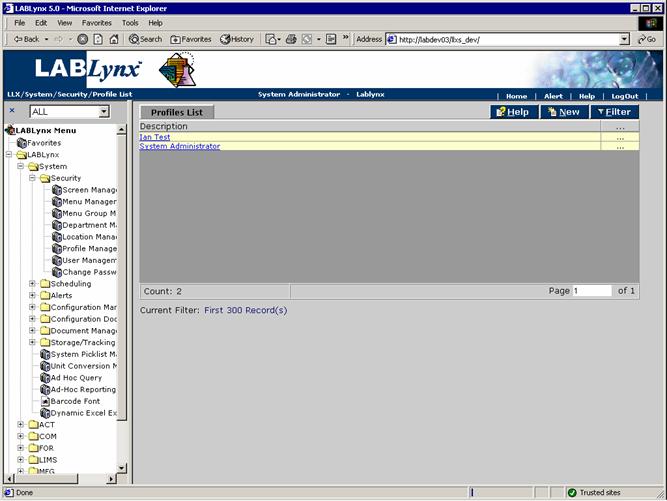
Profile
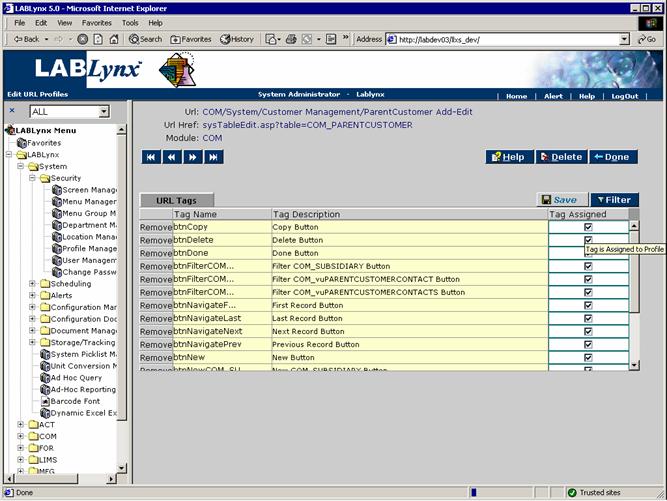
A profile is a set of defined rights. These rights include access to screens. Rights can even be granted to specific buttons or functions within the screens:
For the selected profile, the list of users who have been assigned to that profile are listed. The user may add and edit profiles via the New button or by clicking the URL of one of the available profiles:
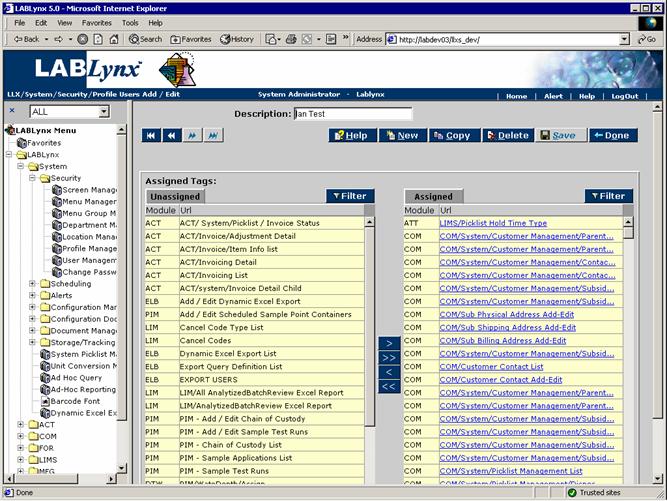
When talking about rights, one example is being able to view user details via the Edit User page. Within this page there are also rights to create a new user, edit (and save) changes to the user details, and to delete (deactivate) a user. The total list of rights is defined as part of the LIMS configuration. Building profiles involves assigning these defined rights to a named profile:
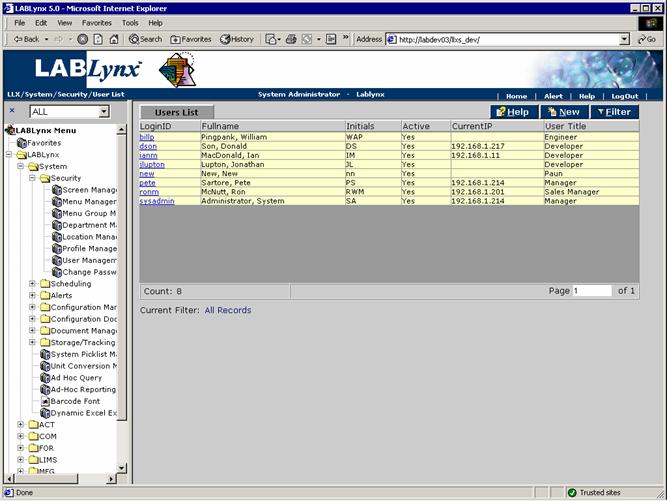
Users list
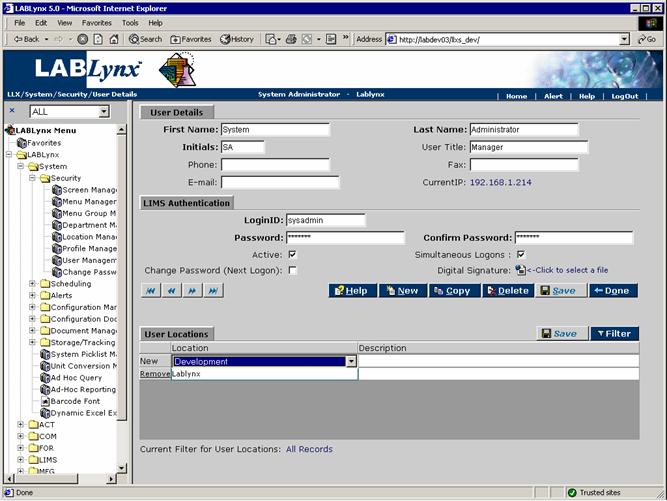
The Users List displays all system users currently defined in the LabLynx enterprise server database. The user viewing this screen will be displayed the user's name and additional administrative information. A user is any person being granted potential access to the LabLynx enterprise server application:
The LIMS will use the users table to track employees. The User Details form allows the LIMS administrator to manage user details such as the user name, initials, login, and password. The user can be authorized to access only one specific location, or the user can be set to access multiple locations. The LIMS administrator must also select the user profile (set of application access rights) for each location and the primary role for the user. The primary role for the user will be the department(s) they are assigned to. The LIMS will store a digitized copy of the users signature for insertion into reports.
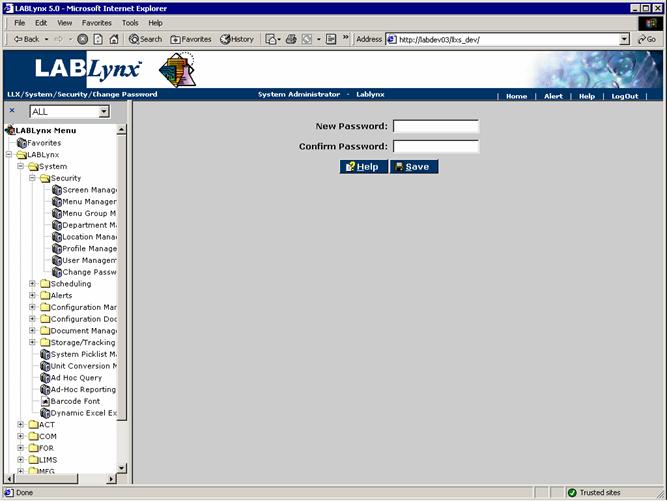
Changing a password
The Change Password screen allows any user with access to the screen to change his or her current password for security access purposes. This screen assumes that the password is being changed for the currently logged in user. The password will be used to authenticate the user at the next login:
System picklist
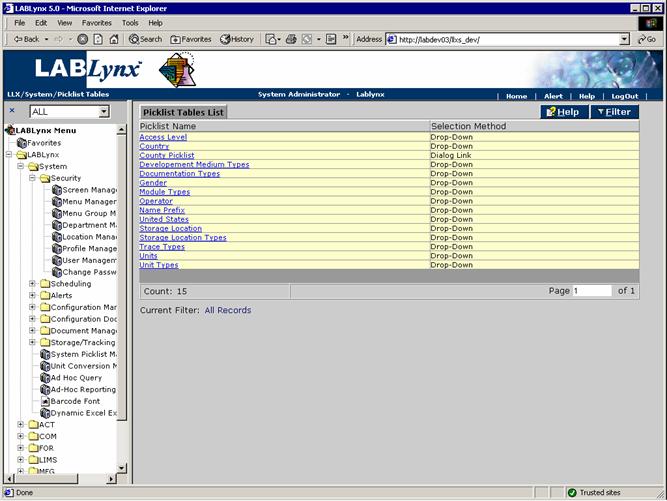
This page allows the LIMS administrator to manage static picklists for use in the various screens, where a list of predefined selections is required for data entry consistency. There are other picklists that are built from data residing in the database and are always dynamic. Certain areas in the system are highly dependent on the configuration of the picklist values; therefore, it is recommended that only system administrators have access to this area.
A list of currently defined picklist types available to add/edit entries for the LabLynx system level is displayed for the user, who may only select a picklist type from the Picklist Tables List. Users are not permitted to add new types to the system. In order to add values to a selected type, the user may simply click on the picklist name, and the system will re-direct to the edit screen for the respective picklist type:
Picklist types allow for the entry of routinely-used values in one place. The children of the picklist types are then displayed to system users (according to the selection method specified on this screen) for simple selection. This also allows the system user simplified data entry by reducing typographical errors.
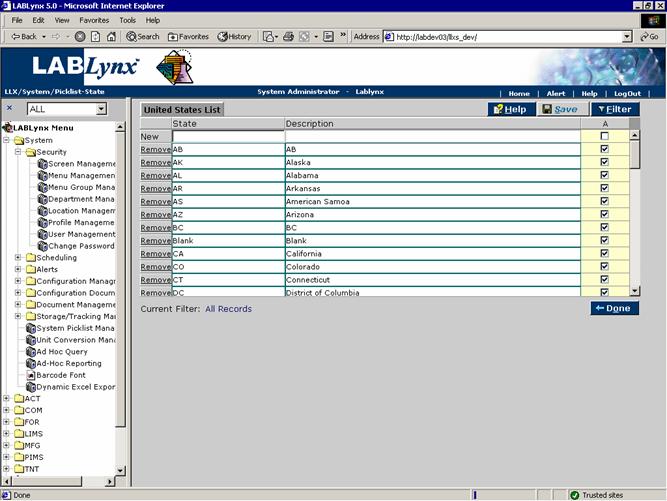
For example, the United States List (shown below) consists of a state name and description. When users are on screens within the system that require a state assignment, they can select from the predefined list instead of manually entering a value. There are multiple picklist set-up areas in the system. They all use the same functionality: